Update: The Evernote security has reported that this issue is resolved.
Evernote for Windows downloads its update information via HTTP, making it subject to man-in-the-middle attacks – further, this allows an attacker to specify an arbitrary file for the updater to download. The good news is that Evernote will not execute the file thanks to signature validation – but the file isn’t removed, so it’s available for later use.
As the file isn’t executed, it isn’t a critical issue.
The update.xml (and the related release notes HTML file) is served over HTTP, not HTTPS; this allows an attacker to control the content of the file. This allows an attacker to indicate that there is an update, and provide a malicious file that the user will download; as the attacker can also control the release notes, the attacker can use that to encourage the user to upgrade (i.e. indicate that it’s a required update).
Evernote will download the file and save it to the C:\Users\<user>\AppData\Local\Evernote\Evernote\AutoUpdate directory, assuming that the malicious binary isn’t signed, the user will be alerted that Evernote was “Unable to download the update” – but the file is left in the above directory.
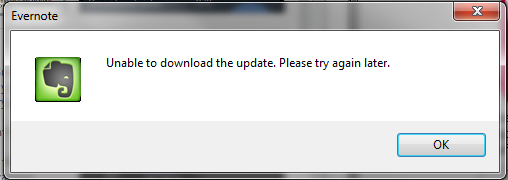
If combined with another issue, it may allow an attacker to gain additional access. This could also be used to plant a file on a victim’s machine (illegal content, false evidence, etc.).
13:37:12 [36468] Command line: "C:\Program Files (x86)\Evernote\Evernote\Evernote.exe"
13:37:21 [33800] AutoUpdate: checking for update at: http://update.evernote.com/public/ENWin5/update.xml
13:37:21 [33800] Received status code 200 when accessing URL http://update.evernote.com/public/ENWin5/update.xml
13:37:21 [33800] AutoUpdate: located update with revision 999999 (local revision is 269614)
13:37:21 [33800] AutoUpdate: selected update with revision 999999
13:37:21 [33800] Received status code 200 when accessing URL http://update.evernote.com/public/ENWin5/relnotes.html
13:37:21 [33800] Evernote is installed PerMachine.
13:37:21 [33800] User is an administrator
13:37:24 [34508] Received status code 200 when accessing URL http://update.evernote.com/public/ENWin5/test.exe
13:37:24 [34508] The update file (C:\Users\<user>\AppData\Local\Evernote\Evernote\AutoUpdate\test.exe) has invalid signature (File has no signature)
13:37:25 [35944] Unable to download update: The data is invalid. (13).