Last night I received an email from Linode about a possible breach and mandatory password reset that reminded me of another recent email, in some disturbing ways.
Dear Linode customer,
Linode administrators have discovered and blocked suspicious activity on the Linode network.
Not too long ago, I received a similar email from Evernote – not just in it’s text, but in the errors made.
Dear Evernote user,
Evernote’s Operations & Security team has discovered and blocked suspicious activity on the Evernote network that appears to have been a coordinated attempt to access secure areas of the Evernote Service.
When I received the email from Evernote, I quickly noticed that the links were to a different site – was it a thinly veiled phishing attempt? With all the links going to links.evernote.mkt5371.com it took a few minutes to work out that the email was actually legitimate. Instead of being able to quickly reset passwords, users were forced to try to figure out if the email was real or not.
When you are sending out a breach notification, it’s critical that users are able to verify, as quickly as possible, that an email is legitimate, and the the call to action really is necessary. Linode, unfortunately, made a similar mistake.
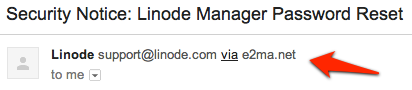
The first thing that jumps out is that it’s from e2ma.net – not Linode directly, next is that the first link in the email points to e2.ma/message/.... These are immediate red flags, the focus instantly switches from taking necessary action to secure a user’s account to trying to figure out if they are being attacked. From comments on their blog post, I’m not the only one that was disturbed by how the email was sent.
Thankfully, they didn’t include a link to the password reset page, and they even told users not to click reset links in unsolicited emails – so it’s not all bad. Users shouldn’t be spending time trying to figure out if a notice is real instead of taking steps to secure their accounts. In situations where there may be a significant security issue, service providers should take every effort to minimize confusion – provide clear information, and make the source as clear as possible.
(Update: See here for more information about what they did wrong, including a vulnerability I found in the password handling of the Android app.)
So the big news today is Evernote being popped; with 50m users and user base that often stores sensitive material – it certainly is a tempting target for many reasons.
Important: Evernote just implemented a service-wide password reset. Please read our post for details and instructions http://t.
It’s time for everyone from the industry, developers, and the government to declare war on ransomware and make it as hard as possible for them to ply their insidious trade. There have been false starts and baby steps, diligent fighters without enough resources, and vendors that have only given a nod to the issue. It’s time to use every tool reasonably available to stop this scourge.
For so many in the industry that have dedicated so much of their time and effort to this fight, this statement may seem to diminish their efforts, but that is not my intent.
Recently a friend of mine asked for input on what would be needed to launch a new security consulting company, to help him out I drafted a detailed list of what would need to be done for a successful launch. Here is an expanded version of that list, hopefully others will find this useful as well. This isn’t the simplest route to setting up a new business, but is intended to set the business up for long-term success.
It has now been over a year since the last major release of YAWAST, but today I am happy to release version 0.7, which is one of the largest changes to date. This is the result of substantial effort to ensure that YAWAST continues to be useful in the future, and add as much value as possible to those performing security testing of web applications.
If you are using the Gem version, simply run gem update yawast to get the latest version.
Whether you are running a bug bounty, or just want a useful way to classify the severity of security issues, it’s important to have a threat-model for your application. There are many different types of attackers, with different capabilities. If you haven’t defined the attackers you are concerned about, and how you deal with them – you can’t accurately define just how critical an issue is.
There are many different views on threat models; I’m going to talk about a simple form that’s quick and easy to define.

