Earlier today, the hacker collective Lulz Security released a batch of 62,156 email/password combinations from unknown sites; I decided to take a look at the data and see if there was anything to be learned from it.
And as always, LulzSec delivers: mediafire.com/?9em5xp7r0rd2y… 62,000+ emails/passwords just for you. Enjoy.
— The Lulz Boat (@LulzSec) June 16, 2011
So, let’s take a look at a few stats:
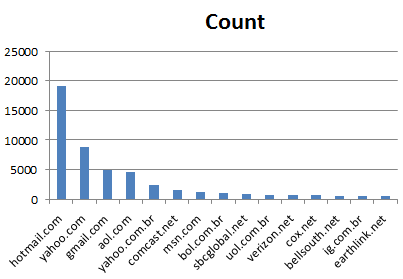
Total Domains: ~5,230
Top 15 Domains:
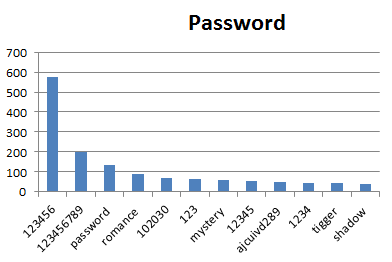
There are over 50,000 unique passwords, but even with this many passwords, there’s still a few quite common – and very bad passwords in use:
While this is a fairly small release, the LulzSec twitter stream has a number of entries like these:
There is some very angry level 85 WoW player cutting his wrists right now, thanks to @miraclejoe and LulzSec. Let it flow…
— The Lulz Boat (@LulzSec) June 16, 2011
There are several tweets about people accessing Facebook, Twitter, and even Amazon accounts – what’s so unfortunate here is that service providers could easily restrict accounts on lists like this to protect the users and greatly reduce the impact of these breaches.
Until people learn that password reuse is dangerous, this will keep happening.
Update: I’ve removed a link to a tweet, as the account has since been removed. The tweet said: “@LulzSec Cheers for the paypal account with £250 in it! ;)”