As a tip for all my Facebook friends, despite the promises you see spreading wildly across Facebook, you can’t see who’s looking at your profile. If you ever see anything like this, it’s a scam – pure and simple:
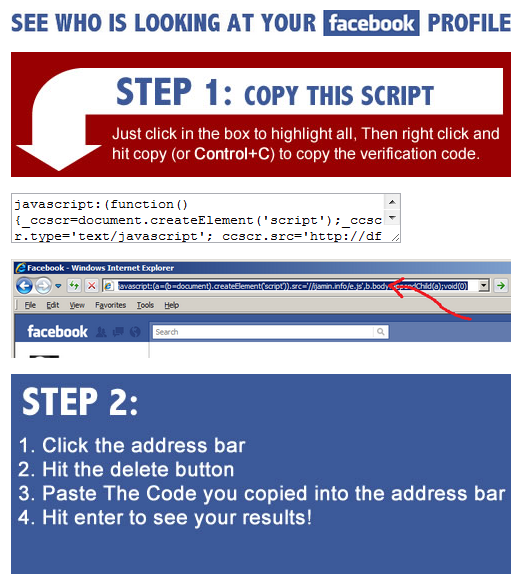
If you ever see a page like this, or one that asks you to paste a script into your address bar as this one does, please immediately report the page. If you see any of your friends ’like’ a page like this or send messages linking to something like this, please warn them – they have likely handed their account over to a scammer or other bottom-dwelling script-kiddy.
If you were unfortunate enough to get a message from a friend and believe what it said; your account is in somebody else’s hands and is being used to spam your friends with a message recommending the same scam to them. Odds are, your account will later be sold to others for spamming – Facebook accounts are sold thousands at a time, and last I saw they go for about $3 each, sometimes more if a person has enough friends.
The best thing you can do if this happens to you is change your password, check the email address and other information listed on your account, then check all of your permissions, including what applications have access to your account. These people move fast, and they can sell accounts several times over, so don’t assume once you change your password all will be good – they’ve probably changed your email address or opened some other means to take your account back so they can keep making money from it.
Be careful and be paranoid, there really are people out to get you.